What is " phishing"????
Phishing which also known as “Fishing”. In other words, it is an online fraud technique used by criminals to entice you to disclose your personal information. Phishing is the fastest rising online crime method used for stealing personal finances and perpetrating identity theft.
Phishers use many different tactics to lure you, including e-mail and Web sites that mimic well-known, trusted brands. A common phishing practice involves "spamming" recipients with fake messages that resemble a valid message from a well-known Web site or a company that the recipients might trust, such as a credit card company, bank, charity, or e-commerce online shopping site.
How will a phishing email/website look like?
Here are provided some example of phishing email and website:
 What to look for in a phishing email ?
What to look for in a phishing email ?
- Generic greeting. Phishing emails are usually sent in large batches. Moreover, the internet criminal will use generic names like "Dear sir/madam" or like "First Generic Bank Customer", so they don't have to type all recipients' names out and send emails one-by-one in order to save time. Therefore, be aware if you do not see your name.
- Forged link. Be aware of the forged link which is provided in email. Usually, it will appear in the email with a link that require you to update the personal information. Furthermore, even if a link has a name you recognize somewhere in it, it doesn't mean it links to the real organization. Also, websites where it is safe to enter personal information begin with "https" — the "s" stands for secure. If you don't see "https" then do not proceed.
- Requests personal information. Usually, some email will request for personal information. Therefore, if you receive an email requesting your personal information, it is probably a phishing attempt.
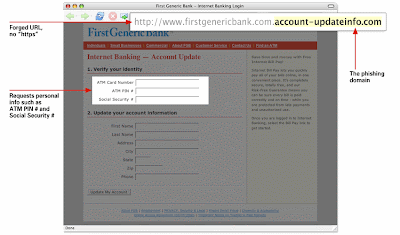 What to look for in a phishing website ?
What to look for in a phishing website ?
- Poor resolution. Phishing websites are often poor in quality, since they are created with urgency and have a short lifespan. If the resolution on a logo or in text strikes you as poor, be suspicious.
Below are some of the recommendation about the prevention method of "Phishing":
Keep antivirus up to date – The most important things you can do to avoid phishing attacks is keeping your antivirus software up-to-date。This is because most of the antivirus vendors have signatures that protect against some common technology exploits. Thus, can prevent things such as a Trojan disguising your Web address bar or mimicking an https secure link. If your antivirus software is not keep up-to-date, you are usually more vulnerable to attack which can seize your Web browser and put you at risk.
Do not click on hyperlinks in e-mails – Never! Never! Never click on any hyperlink in an e-mail, especially from unknown sources. You never know where the link is going to really take you or whether it will trigger malicious code. Moroever, some hyperlinks can take you to a replicate HTML page that may try to scam you into typing private information. If you really want to check out the link, manually retype it into a Web browser.
Take advantage of anti-spam software – Anti-spam software can help keep phishing attacks at a minimum. A lot of attacks come in the form of spam. By using anti-spam software such a Qurb, the phishing attacks can be reduced because the messages will never end up in the mailboxes of end users.
Pay attention to your billing cycle. If credit card or utility bills fail to arrive, contact the companies to ensure that they have not been illicitly redirected.
Use anti-spyware software –Keep spyware down to a minimum by installing an active spyware solution such as Microsoft Antispyware and also scanning with a passive solution such as Spybot. If for some reason your browser is hijacked, anti-spyware software can often detect the problem and provide a solution..
References:
http://antivirus.about.com/od/emailscams/ss/phishing.htm
http://www.phishtank.com/what_is_phishing.php?view=website
http://mcobit.business.nd.edu/phishing.cfm

 Phishing is one example of social engineering and it is a technique used to gain personal information such as account number and passwords by sending fraudulent e-mail messages to e-mail users.
Phishing is one example of social engineering and it is a technique used to gain personal information such as account number and passwords by sending fraudulent e-mail messages to e-mail users.





